
CIO Says: Free At Last!"Finally, I can get out from under the tedium and challenges of IT operations and simply harness cloud computing to meet my organization's computing needs." | CIO Says: There's No Free Lunch"Cloud computing is more complex than the marketplace acknowledges. Before I do anything with third-party cloud services, I'd better do my homework." |
"Cloud computing is still evolving and represents a large ecosystem of many models, vendors, and market niches. It is this breadth that is its virtue and its vice."
-- Ron Blitstein, Guest Editor
Opening Statement
Rows and flows of angel hair,
And ice cream castles in the air,
And feather canyons everywhere,
I've looked at clouds that way.-- "Both Sides Now" by Joni Mitchell
The interesting thing about Cloud Computing is that we've redefined Cloud Computing to include everything that we already do.... I don't understand what we would do differently in the light of Cloud Computing other than change the wording of some of our ads.
-- Oracle CEO Larry Ellison, as quoted in Wall Street Journal, 26 September 2008
Despite the hype, cloud or utility computing is not a new concept. It involves organizing and providing a wide range of computing-related services in much the same way as public utilities deliver services like electricity, water, and gas. In fact, the underlying concept of cloud computing dates back to the 1960s, when computer scientist John McCarthy suggested that "computation may someday be organized as a public utility."
For more than 50 years, utility or cloud computing remained only a concept. Now thanks to advances in storage and server virtualization, grid computing, and automated provisioning -- not to mention marketing prowess -- cloud computing is not only very real, but the hyperbole surrounding it has created such profound distortions as to muddle the mind of the most discerning CIO or CTO. The fact is that cloud computing now means whatever the last brochure said it means, ranging from elastic provisioning to the illusion of an infinite supply of all things computational, instantly available, supplied at rock-bottom prices with high quality.
CLOUD COMPUTING DEFINED
A few definitions are in order before we continue. In many ways, third-party cloud computing extends the earlier concept of colocation facilities (Co-Lo). For some, Co-Lo offered significant benefits in the areas of large-scale power, cooling, fire suppression, telecom connections, and mechanical systems. The big idea was that if data center infrastructure and communications facilities were "professionally" maintained by a third-party service provider, IT operations personnel could redirect capital investment to address higher-order computing challenges.
Cloud computing moves the provider's service to a higher level of support. It provides on-demand network access to a shared pool of configurable computing resources (networks, servers, storage, and applications) that can be rapidly provisioned and released with minimal effort. The cloud model has several essential characteristics, which include on-demand self-service, broad network access, resource pooling, rapid elastic computing, and measured service.
As depicted in Figure 1, cloud computing adds three service models to the Co-Lo construct and includes such service archetypes as software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS).
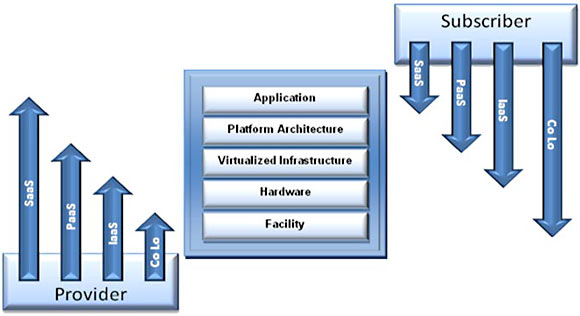
Figure 1 -- Cloud computing. (Adapted from the US NIST model.)
It is worth taking a few moments to describe the differences in accountability associated with each cloud service model. For IaaS, the cloud provider is responsible for providing, configuring, and deploying processing, storage, networks, and other resources where software may be installed and run. The subscriber does not manage or control the underlying cloud infrastructure but does control operating systems, storage, and deployed applications and may have limited control of select networking components like host firewalls. Security provisions beyond the basic infrastructure are also the responsibility of the cloud subscriber.
In the case of PaaS, the subscriber deploys onto the provider's cloud infrastructure business applications created using programming languages and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure (including network, servers, operating systems, or storage) but has control over the deployed applications and possibly application-hosting environment configurations. Security responsibilities tend to be shared between the provider and the subscriber.
For SaaS, the subscriber uses the provider's applications, which run on the provider's infrastructure. The applications are accessible from various client devices through a thin client interface such as a Web browser. The subscriber does not manage or control the underlying cloud infrastructure (including network, servers, operating systems, storage, and even individual application capabilities), with the possible exception of limited user-specific application configuration settings. The subscriber may make preference selections as well as make minor changes to administrative application settings. Security provisions are principally carried out by the provider.
Regardless of service model, cloud computing also has four deployment modes: private clouds, community clouds, public clouds, and hybrid clouds. A public cloud is one in which the infrastructure and other computational resources are made available to the general public over the Internet. It is owned by a cloud provider selling cloud services and, by definition, is external to an organization. At the other end of the spectrum are private clouds. A private cloud is one in which the computing environment is operated exclusively for an organization. It may be managed either by the organization or a third party, and may be hosted within the organization's data center or outside of it. A private cloud gives the organization greater control over the infrastructure and computational resources than does a public cloud.
Somewhere in between public and private clouds live the other two deployment approaches: community clouds and hybrid clouds. A community cloud is similar to a private cloud, but the infrastructure and computational resources are shared by several organizations that have common privacy, security, and regulatory requirements. It may be managed by the organizations or a third party and may exist off premises for all, or a single community member may elect to host the community cloud for all members. A hybrid cloud is a composition of two or more clouds (private, community, or public) that remain unique entities but are bound together by standardized or proprietary technology that enables interoperability.
Cloud computing is still evolving and represents a large ecosystem of many models, vendors, and market niches. It is this breadth that is its virtue and its vice. Cloud computing definitions, use cases, underlying technologies, issues, risks, and benefits need to be understood through debate and limited risk trials before industry, government, and NGO stakeholders can move forward responsibly to exploit this computational form.
Cloud computing technology introduces new dimensions to the challenges of security, privacy, interoperability, portability, data remanence, auditability, and compliance. These elements, along with the absence of certification requirements for cloud services, are major barriers that must be overcome to promote broad adoption.
Though the cloud computing model offers the promise of significant cost savings coupled with increased IT agility, it is essential that organizations not only carefully consider how and where to apply this approach, but also understand the implications to the rest of the IT ecosystem. Simply accelerating server provisioning will not deliver improved time to market for IT solutions. The IT system must move in synchrony. And that is the focus of this issue of Cutter IT Journal.
We begin with an article by Cutter Senior Consultant Bill Keyworth, who shows us how to "manage through the hype" surrounding cloud computing by asking a series of straightforward evaluative questions. He addresses due diligence for selecting cloud suppliers and reminds the reader that differing internal processes are required based on the cloud service being provided. Keyworth focuses on the need to understand your cloud supplier's ability to fulfill capacity planning, compliance management, and disaster recovery commitments as well as your own ability to establish effective performance incentives and penalties. Finally, he stresses the importance of confirming that your cloud security and risk management tools can satisfactorily protect your newly integrated computing infrastructure and existing corporate data from malicious intent.
Next, Cutter Senior Consultant Claude Baudoin discusses how cloud computing changes the landscape of organizational interactions and suggests approaches to help CIOs get in front of business partners and procurement organizations in order to move past stale perspectives and use the cloud as a mechanism to rekindle productive relationships. In addition, he offers a view of the key roles and accountabilities that IT must retain regardless of how it approaches the cloud.
Our third article is by Cutter's EA Practice Director Mike Rosen, who provides an architectural assessment of cloud computing. As Rosen observes, "Taking an architectural approach to the cloud means looking at the promises and opportunities of the cloud from ... [an] enterprise perspective." IT resources provided through the cloud do not exist by themselves. They become part of the enterprise's computing ecosystem and as such must add value -- not complexity, unnecessary redundancy, inconsistency, cost, or new sources of weakly understood risk. He provides a pair of matrices that will be useful as you consider computing in the cloud.
Malcolm Fry pens our fourth article, probing the question of whether public or private clouds help or hurt IT's efforts at achieving higher levels of operational excellence. Along the way, Fry examines the key attributes of cloud suppliers that CIOs must assess and evaluate. Importantly, he observes that though there is no specific standard that applies exclusively to cloud computing, many complementary standards and frameworks can and should be employed when evaluating suppliers. He reminds us that it is the responsibility of CIOs to ensure that the correct level of standards are applied to any cloud service upon which their enterprises depend. To help CIOs determine the appropriate level of standards to apply, Fry offers this "litmus test" question: "What is the potential impact if a cloud service fails?"
Finally, I provide an overview of the security and privacy challenges of public cloud computing and describe various considerations that organizations should take into account when outsourcing data, applications, and infrastructure to a public cloud supplier. I explore the seldom discussed upside of cloud security as well as the often decried negatives, touching on such issues as compliance, trust, identity and access management, data protection, system availability, and incident response.
As you delve into this issue, I hope you will take away a few key points that can help you succeed in the cloud:
-
The security and privacy aspects of public cloud computing require careful study and planning. The same is also true of compliance challenges associated with private clouds.
-
Before embracing public clouds, take the time to truly understand the vendors and their experience and ability to deliver a cloud solution that will satisfy your organization's security and privacy requirements.
-
Do not relinquish accountability for privacy and security of data and applications deployed in public clouds. Strong management practices are essential for operating and maintaining a secure cloud computing solution. The audit committee of your board of directors will thank you.
-
Remember that you retain responsibility for the end-to-end solution, so maintain vigilance on security risk for client-side computing components as well.
ABOUT THE AUTHOR
Though the cloud computing model offers the promise of significant cost savings coupled with increased IT agility, it is essential that organizations not only carefully consider how and where to apply this approach, but also understand the implications to the rest of the IT ecosystem. Simply accelerating server provisioning will not deliver improved time to market for IT solutions. The IT system must move in synchrony. And that is the focus of this issue of Cutter IT Journal.








