Find analysis of data from Cutter's ongoing industry research efforts, brief treatments of topics that don't require the in-depth research of an Executive Report, updates on previously-covered topics, and more, in 2-4 page Executive Updates.
You Have the Right to Decide, Influence, or Just Watch: Governance Where IT Counts
Technology governance is something every company needs. But it's also something that most companies would prefer not to discuss -- or publish. The fact is that without explicit, consistent, well-communicated and well-supported governance, you will experience some degree of chaos in the technology acquisition, deployment, and support process.
Corporate Adoption of On-Demand/Cloud-Based BI and Data Warehousing: Implementation Trends and Impact
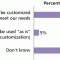
In June-July 2009, Cutter Consortium conducted a survey that asked 79 end-user organizations about their various BI and data warehousing efforts, including the use of various on-demand/cloud-based BI and data warehousing solutions.1
Architectural Requirements of the Hybrid Cloud
Cloud computing continues to gain momentum as a description of service offerings based on a virtualized data center infrastructure and provided over the Internet on an as-needed basis. Public clouds, such as Amazon EC2, first brought attention to this model, followed by private clouds built within an organization, as exemplified by IBM's Blue Cloud initiative.
Key Strategic Trends for 2010
Forecasting trends is a perilous exercise, particularly in times of great uncertainty. We are in the midst of revolutionary technological change within an uncertain economy. For decision makers, the result is unease, as we throw the die and bet either on embracing new opportunities or remaining with the status quo.
Social Media Comes of Age: Time to Listen to the Kids
Social media is everywhere.
Wikipedia -- the ever-popular encyclopedic wiki -- describes social media as follows: 1
IT Project Management Confidential: Transcending Traditional Project and Product Methodologies
I must first confess. I've only skimmed the nearly 400 pages of the PMBOK Guide, and I'm not a PMI-certified PMP.1 If I decided to sit for the certification exam, I'm not entirely confident that I would pass.
Size and Structure of the EA Department
Enterprise architecture (EA) managers often wonder about the best way to organize the EA department, but before addressing that issue, we first must answer the question, "How many architects do we need in the first place?" Of course, there is a difference between needing them and getting the budget for them.
SOA, BPM, MDM: Notes from the River Walk
IT Outsourcing: Provider Selection and Implementation
When an organization decides to hire an outside IT provider, it first must review its previously established IT requirements and set guide
Emerging Social Networking Applications
Web 2.0 and social networking sites are continuing to develop in response to user needs. They provide an important new form of communication and social interaction with numerous repercussions in the world outside, as reflected in recent stories about Facebook and YouTube celebrity and use in the 2008 US presidential campaigns.
Corporate Adoption of On-Demand/Cloud-Based BI and Data Warehousing: Status and Directions
Organizations today have the option of choosing from a variety of on-demand or cloud-based BI and data warehousing solutions. These range from reporting, dashboards, and focused analytic applications offered as licensable services to hosted data integration services and full-blown managed data warehouses.
Security, Privacy, and Compliance: Bridging the Gap
An evolution in the nature, methods, and motivation behind perpetrating security breaches has had a profound impact on the business environment. This shift has caused a fundamental altering in the way that an enterprise views information security, privacy, and compliance. The ever-growing compliance framework being built around those concerns fuels the need for the convergence of these disciplines within the enterprise in a more holistic manner than previously imagined.
The Great Divide: Fix My Computer, Fix My Business -- Every Other Weekend
IT is separating as we speak. For some, IT is about desktops, servers, and networks. For others, technology is about data, customers, and revenue. These two perspectives represent entrenched cultures about technology's primary role. Once you identify the dominant culture, you can determine the kind of technology your company wants.
Midweek in the Garden of Good and Evil: Corporate Social Responsibility in the Age of Google
As I flew out of Los Angeles International Airport on my final leg of a late evening flight back home to the Midwest, I gazed in awe at the sprawl of the second-largest city in the US unfolding outside my window. At 5,000 feet, now circling, now climbing, I observed millions of tiny points of lights as far as the eye could see.
Adopting Social Media: Projections, Pilots, and Politics
Enterprise adoption of social media usually hinges on three factors: financial projections, pilot results, and politics. Financial projections are based on spreadsheet models. Pilot efforts, often called proof-of-concept efforts, study the real-life effects of the innovation. But the effort involves resource allocation, and that's where politics enters.
The Ontology of Intelligent Agents
The term "agent" is used as an anthropomorphic metaphor. Such figures of speech serve a purpose in that they are beneficial for human-machine interaction and for developing high-level abstractions of information structures. The metaphor "agent" has a social origin (e.g., travel agent). It falls in line with the emergence of the Internet as a social phenomenon. The Internet houses an enormous number of autonomous individuals and entities with varying degrees of intelligence and autonomy interacting with one another.
The Retained Organization: Managing the Hybrid Sourcing Solution
A hybrid of outsourcing and insourcing is the most common sourcing strategy for information and communications technology (ICT) in organizations today. It's very rare to see an organization that has outsourced 100% of its ICT needs to third parties; likewise, it's rare to see one that keeps everything inside.
The Acquisition of Innovation
The pursuit of innovation remains one of the cardinal issues of business today. Innovation is viewed as the secret ingredient permitting companies to grow, to remain competitive, and to develop products and strategies capable of ensuring the firm's survival. Yet internal innovation is fraught with problems. Ideas abound, but the essential screening and testing processes are both costly and uncertain.
Advances in Semantic Collaboration
Imagine going to the office in the morning, switching the computer on, and finding updates on your desktop that summarize what coworkers and colleagues in your organization and in your wider professional network have been up to. When someone in your network makes a change or uploads or downloads a file that is relevant to you, you'll be notified.
SAML: "Beyond the Intranet" SSO Solution
Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authentication and authorization data between security domains. SAML is a product of the OASIS Security Services Technical Committee. The single most important problem that SAML was created to solve is the Web browser single sign-on (SSO). However, there are limitations to SAML 1.1 for that purpose. In fact, the problem that SAML 1.1 solves more efficiently is the authentication and authorization of SOAP Web services by using SAML as a WS-Security token.