Find analysis of data from Cutter's ongoing industry research efforts, brief treatments of topics that don't require the in-depth research of an Executive Report, updates on previously-covered topics, and more, in 2-4 page Executive Updates.
Service-Oriented Architecture: Strengths and Weaknesses
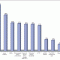
This is the third in a series of four Executive Updates in which I am analyzing the results of a recent Cutter Consortium survey on service-oriented architecture (SOA).
Business Modeling and Analytics
Business modeling currently describes a vast territory with conflicting purposes, methods, and outcomes. Some of the confusion is historical -- as between financial modeling and models created specifically for software development, for example.
Synthesis of Lean, Mindful, and Agile with the Theory of Constraints
A May 2006 article in APICS magazine describes the search by a California-based global electronics manufacturer for the best approach to continuous improvement.1 The company found that the right combination of the Theory of Constraints (TOC),2 Lean, and Six Sigma3 led to the most effective long-term results (see sidebar "In Search of the Best Approach").
Controlling Risk in Automated Modernization Projects
An automated modernization project (also referred to as a conversion, a migration, or a legacy renewal project) is inherently different from most projects that IT professionals will participate in during their careers -- in several different ways. When this specialized type of project goes awry, it is almost always due to a failure to appreciate these differences and to allow for them in the project plan.
SaaS Appeal Growing
In late 2005 and early 2006, Cutter Consortium published a series of Executive Updates 1 based on the results of its first software-as-a-service (SaaS) survey, which dispelled many of the misconceptions about the relatively new phenomena at the time.
Using Video Games to Enhance Training
Gaming and simulation have been used for some time in education as "edutainment" -- from model UN and political scenarios in high schools to courtroom reenactments for those studying law. In business, role-playing games and simulations have long been a part of management training. Today, gaming and simulation are reaching entirely new levels and new audiences as they go online and merge with the vast and ever-growing video gaming sector.
Revisiting the "IT Doesn't Matter" Argument
There were inklings of technology concern in the early 1990s, but they all disappeared when the Internet intoxicated everyone. But since 2000, there have been a series of challenges about the value of information technology, about whether or not IT is still really important. Paul Strassmann, for example, has argued for years that investments in technology do not predict profitability or growth (www.strassmann.com).
Running Your EA Practice Like a Business: A Holistic Approach
Imagine a perfect world where everything works just fine -- all goes as planned and nothing goes off track. For a CIO attempting to deliver business solutions in today's IT world, there is no such thing as a perfect world. Most CIOs and other practitioners involved in making business decisions willingly agree on one thing: change is the only constant fact in their world.
BI in the 21st Century: Models for Dynamic Real-Time Business Optimization
Let's anticipate where we'll all be in 10 years and then try to figure out how to get there. As more technology becomes commoditized and continues to deliver reliable, secure, and "always on" services, the role it plays in the early 21st century will continue to change dramatically. Twenty years ago, we said it was all going to be about the data; 20 years from now, it's all going to be about information, knowledge, and the intelligence they enable.
The Agile Path
It does us no good to look for enemies in software development, or even victims to be protected from the enemies. When we presume there is a Them that is somehow set against an Us, we are already subtly creating a barrier that creates Them. We are alienating people, which is rarely helpful. We may not realize we are doing it, but the damage (and missed opportunity) is still real. Unfortunately, the early years of the agile movement have been divisive -- full of battle lines of one kind or another. Many of us have artificially divided software development into "agile" and "not agile" -- as if agility were somehow binary.
Internal IT Controls Above and Below the Border: SOX and Canada's Bill 198
It has sometimes been said of the US and UK that they are two nations separated by a common language. In some respects, the same can be said about Canada and the US. Upon crossing the border, miles turn to kilometers, gallons to liters, and a dollar (although still called a dollar) buys more or less, depending on which direction one is headed.
Business Process Outsourcing Risks: A Multitude of Flavors
Theoretically speaking, there is nothing in business that cannot be outsourced. This extreme view sees an infinite, irreversible trend of more and more business activities being outsourced, from as early as when power supply was outsourced to specialist power plants, which most companies of the world now take for granted. In the context of IT, the ever-increasing scope of outsourcing remains controversial. The focal point of this controversy lies within business process outsourcing (BPO).
Wiki Cool and Effective Technology
Some of the big technologies, the ones with the deepest impact on the everyday work lives of people, prove to be some of the least complex to learn and use. Think e-mail and the word processor. After having mastered these tools, you stand back and ask the question every meaningful innovation begs: why didn't someone invent these sooner? So too will users demand an answer to this question: couldn't someone have invented the corporate wiki years ago, when I could have first used it?
A Pragmatic Approach to Implementing ITIL: Part I -- Getting Started
This Executive Update, the first in a series of two, provides an overview of the methodology and approach used to develop detailed business processes for managing an IT environment. A real-life case study using an approach for creating service management processes and subprocesses is presented, and the interfaces needed to support application development migration are identified. Finally, an example process model as well as process flows are included.
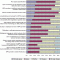
Service-Oriented Architecture: Strategies and Implementation
This is the second of four Executive Updates in which I shall be analyzing the results of a recent Cutter Consortium survey on service-oriented architecture (SOA).
Methodology Object Management and Quality Assurance
In a 2004 Cutter IT Journal article, Methodology Object Management (MOM) was introduced to fit an entire range of software development processes -- from the "heavy" traditional waterfall approach to "light" agile development methods [2]. MOM's basic tenets were developed for IT organizations that have multiple development cultures but aspire to manage the overall development structure consistently -- regardless of the software technique used in the various business lines.
Best Practices in ERM
There is no single best practice that is appropriate for all areas of risk associated with IT. Each risk area has a number of practices that should be considered. In this Executive Update, I focus on the following three areas:
Business strategy risks
Compliance risks
Process risks
The Configuration Concept: Supplier Grouping
This Executive Update is the second in a series that examines information and communications technology (ICT) outsourcing and its various configuration options. The series is based on a recent Cutter Consortium survey of 73 organizations in 25 countries across the globe. 1
Sun's New Business Model
Sun Microsystems has released its operating system (Solaris 10) and Java Enterprise System (JES) under a new subscription scheme in which the customer gets the entire enterprise software stack for free, and support is charged on a per-employee-per-year basis instead of the typical per-processor-per-user model. The JES contains Sun's portal server, application server, identity server, Web server, clustering software, and some other similar products.
Conversing Across the Cultural Divide
Cultural misunderstandings can bring globalization to a halt! OK, that statement is a little dramatic, but you may have had this type of confusion bring some of your projects to a halt. Knowing how to avoid cultural communication misunderstandings is a competitive advantage. Thus, this Executive Update reviews three main global communication styles and offers steps on how to use this knowledge to reduce cultural snafus.
Locking into Software-as-a-Service
One of the most persistent truths of information technology is the phenomenon called lock-in. Lock-in describes the fact that technology platforms do not naturally interoperate and that as users make commitments to specific platforms, they are "locked-in" to their decisions. This concept has collected a lot of dust over the years seeing as IT managers have endured this reality since the beginning of automation.
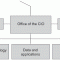
Just Enough Organization
Lots of companies wrestle with organizational structure. Consultants and gurus have all sorts of ideas about how to organize technology in just about every company in the world. But what should the basics look like? What are the pieces that should work for just about all companies -- regardless of their vertical industry?
There are five primary pieces -- all under the authority of the office of the chief information officer (CIO):
A governance organization
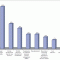
Service-Oriented Architecture: Awareness and Plans
Five years have passed since service-oriented architecture (SOA) started to become the IT industry's favorite new topic, displacing older paradigms such as client-server, object orientation, and transaction processing. When making critical decisions about future architecture and procurement plans, it is especially desirable to obtain as many hard facts as possible; so Cutter Consortium recently conducted a survey to establish what IT user organizations are thinking and doing about SOA.
Podcasting and Defamation in the US
Podcasting is the distribution of audio and/or video content via the Internet on a subscription basis.