AMPLIFY VOL. 37, NO. 2

The importance of cybersecurity in space exploration cannot be overstated. Spacecraft, satellites, and other space-based systems are increasingly dependent on interconnected technologies. These systems, which control aspects of space missions from navigation to life support, are potential targets for cyber threats. The ramifications of a security breach in such environments range from data loss and compromised missions to the endangerment of human life.
Artificial intelligence (AI) integration is essential for the success and safety of missions, but this reliance brings additional cybersecurity challenges. AI offers groundbreaking capabilities in automating complex tasks, analyzing vast amounts of data, and making autonomous decisions based on real-time environmental inputs. However, as AI becomes more sophisticated and autonomous, the risks evolve to include malicious AI behaviors, data integrity issues, and the exploitation of AI systems for unauthorized control or sabotage.
On the flip side, AI can be a powerful tool in enhancing cybersecurity. AI algorithms can be used to continuously monitor satellite networks and spacecraft so anomalies and potential threats can be detected in real time. AI can also aid in predictive analysis, helping identify and mitigate potential vulnerabilities before they are exploited.
Addressing these cybersecurity challenges is essential to protecting valuable space assets, ensuring their longevity, and safeguarding the future of space exploration. This article provides an overview of the cybersecurity landscape in space exploration and looks at the increasing role of AI in space exploration. Developing robust cybersecurity strategies to protect these advanced systems is essential to ensuring that mankind’s journey into the final frontier is innovative and secure.
Cyber-Threat Landscape in Space Exploration
Space exploration’s rapidly evolving cybersecurity landscape includes:
-
Cyber espionage, which can lead to the loss of sensitive or proprietary technological data, undermining national security and economic interests
-
Sabotage of space infrastructure, which can result in mission failure, loss of expensive equipment, and endangerment of human life
-
Ransomware and malware attacks, which can corrupt data, disrupt operations, and cause significant financial losses
-
Increasing involvement of private companies and international collaborations, introducing new security challenges
-
Cyberattacks that impact research activities and scientific data integrity, hindering international cooperation in space exploration
It’s difficult to determine the frequency of cyberattacks. For one thing, a significant portion of advancements and vulnerabilities in space cybersecurity, especially those tied to military or national security, are classified. Additionally, there is a considerable delay between when a new vulnerability is identified or a defense mechanism is developed and when this information is made publicly available. The delay gives space agencies and cybersecurity professionals time to implement countermeasures before vulnerabilities can be exploited.
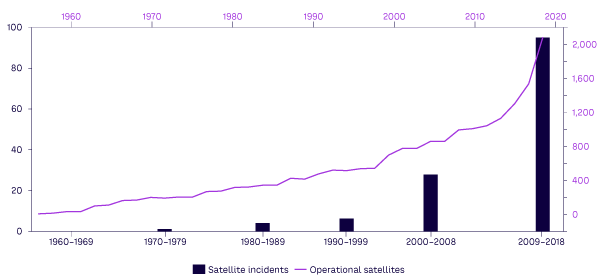
Despite these data-access issues, there is no disputing the problem. In 1970, there were 200 operational satellites and one incident. In 2018, there were 2,100 operational satellites and 95 incidents (see Figure 1).1 Expert predictions vary; the US Government Accountability Office (GAO) estimates there will be an additional 58,000 satellites in orbit by 2030,2 with an accompanying rise in incidents. Many operators, facing the growing specter of these attacks and the inadequacy of their defenses, choose silence over disclosure. This underreporting not only masks the scale of the issue, it points to widespread unease about existing vulnerabilities in space systems.
Satellites Under Siege: Jamming, Spoofing & Data Hijacking
Satellites are increasingly being targeted by bad actors using a variety of methods:
-
Jamming. This was evident in 2014 when a suspected Russian jamming attack disrupted GPS systems in Norway, impacting civil aviation navigation.3 The incident demonstrated how jamming could lead to significant economic disruptions and pose risks to public safety.
-
Spoofing. In 2013, a University of Texas at Austin team demonstrated the ability to mislead the navigation system of a yacht by spoofing GPS signals.4 This kind of attack could lead to misdirected satellites, causing data inaccuracies or space collisions.
-
Data hijacking. In 1998, hackers assumed control of the US-German-UK ROSAT (short for Röntgensatellit) x-ray satellite and commanded the satellite to point its solar panels directly at the sun, causing irreversible damage. This incident underscored the potentially dire consequences of such attacks.5
AI’s role in satellite systems magnifies these types of risks. For example, AI-driven navigation systems, if spoofed, could provide false data leading to incorrect satellite positioning. Similarly, data hijacking of AI-driven satellites could compromise the integrity of data analysis and decision-making processes, which are critical to space missions.
Implementing advanced security measures in space systems is challenging due to limited onboard processing power and bandwidth constraints. This necessitates innovative solutions that provide robust security without overwhelming the system’s resources. For instance, lightweight cryptographic algorithms are being developed to secure communications without imposing significant computational loads.
Spacecraft Vulnerabilities: Hacking Life Support, Navigation & Propulsion Systems
Spacecraft are becoming increasingly susceptible to cyberattacks, posing a significant risk to mission success and astronaut safety:
-
Life support. If the life support system aboard a manned spacecraft is hacked, it could fail to maintain essential environmental conditions. For example, manipulating oxygen levels or temperature control systems could create life-threatening conditions.
-
Navigation. A cyberattack on a navigation system could lead to loss of control and direction. Because these systems rely heavily on software and satellite communications, they are vulnerable to attacks that alter their trajectory enough to cause a crash. Such an event would jeopardize the mission and create space debris, creating a risk to other space assets.
-
Propulsion. The complexity and automation of spacecraft propulsion systems create many entry points for cyberattacks, and compromising these systems could be catastrophic. If hackers alter thrust or direction, the spacecraft will deviate from its intended path and could crash.
Ground Control Security: Safeguarding Ground Stations & Network Communications
Ground stations and network communications systems link space assets and their operators. Securing these channels is critical to the operational integrity of space missions:
-
Ground stations. These are susceptible to both physical and cyber threats. The stations often use standard communications protocols, making them targets for denial-of-service attacks that can disrupt operations, leading to loss of control over space assets.
-
Communications links. Interference with these links can lead to a loss of communications, leaving spacecraft unable to receive vital commands or transmit data back to Earth. Bad actors can target these links to intercept, manipulate, and/or disrupt the flow of information.
-
Network security. Any breach in the security of the networks used for space communications can lead to leaks of sensitive information and/or operational disruption. Advanced encryption and secure communications protocols are necessary to protect these networks from unauthorized access.
Addressing the vulnerabilities in spacecraft systems and ground control networks requires combining physical security measures with advanced cybersecurity strategies, including regular software updates, continuous monitoring for anomalies, and robust encryption methods.
The Insider Threat: Human Error & Malicious Intent in Space Systems
Insider threats encompass both human error and intentional malicious activities. These risks stem from individuals with authorized access to space missions’ critical systems and data.
Simple mistakes by staff, such as system misconfiguration or erroneous command inputs, can have drastic consequences in the highly sensitive environment of space operations. For instance, an incorrect data entry or a misconfigured network setting could compromise the safety of a spacecraft or lead to the loss of critical mission data.
Mitigation requires a combination of stringent security protocols, continuous monitoring, and regular audits of system access and activities. Employee education on cybersecurity best practices and implementing a least-privilege access policy can enhance protection.
Space Communications: Key Vulnerabilities in Satellite Networks & Spacecraft
Satellite networks and spacecraft form the backbone of space communications systems. Identifying and addressing their vulnerabilities is crucial to ensuring the security and functionality of space missions.
For example, signal interference, whether accidental or deliberate (jamming), can disrupt the transmission of critical data and commands. The onboard systems of satellites and spacecraft (navigation, propulsion, and communications subsystems) are also vulnerable to cyberattacks. These systems might have outdated software or unpatched vulnerabilities that can be exploited.
Inadequate encryption of communications signals makes satellites susceptible to eavesdropping and data manipulation. This poses a significant threat, especially for military and strategic satellites. Ground stations, which control and monitor satellites, can also be attack targets, leading to the loss of control over satellites or corruption of the data being relayed.
Mitigating these vulnerabilities requires frequent updating and patching of onboard systems, employing advanced encryption techniques, and deploying robust cybersecurity measures to secure ground stations.
Real-World Cybersecurity Incidents in Space Missions
Cyberattacks have been a risk for many years and are multifaceted, as the following examples show. They underscore the critical need for robust security measures in the space exploration realm.
NotPetya Attacked Ukrainian Infrastructure
The 2017 NotPetya cyberattack, though primarily targeting Ukrainian infrastructure, indirectly affected satellite communications systems and their ground facilities worldwide.6 The attack exploited vulnerabilities in terrestrial infrastructure and serves as a stark reminder of the interconnected nature of space- and ground-based systems.
The incident illuminated the vulnerability of critical infrastructure, including space-related systems, to widespread cyberattacks. It also underscored the need for the space industry to bolster cybersecurity measures, recognizing the cascading effects that terrestrial cyber threats can have on space operations.
NotPetya’s impact extended to satellite companies, possibly through compromised software suppliers, highlighting the intricacies and vulnerabilities within the modern supply chains of the space sector. This aspect of the attack demonstrated the need for rigorous security protocols throughout the supply chain.
SpaceX Starlink Terminals Were Jammed in Ukraine
In 2022, SpaceX’s Starlink satellite communications terminals, supplied to Ukraine during the conflict, experienced targeted jamming attacks.7 This event marked a significant instance of cyber interference in satellite communications within a geopolitical conflict zone.
The incident underlined the strategic importance and vulnerability of satellite communications systems in modern conflicts. SpaceX’s prompt response demonstrated the necessity for agility and resilience in satellite communications networks against evolving cyber threats.
China-Based Hackers Infiltrated Satellite & Telecoms
In a sophisticated campaign in 2017 and 2018, hackers based in China infiltrated satellite operators, defense contractors, and telecoms companies in the US and Southeast Asia.8 The campaign, identified by Symantec, involved targeting computers used for satellite control and geospatial imaging software.
The focus on operational systems suggests that the attackers aimed to intercept (and possibly alter) communications traffic, which could have led to significant disruptions in consumer and business activities.
The hackers employed a technique known as “living off the land,” using legitimate tools and system features to blend malicious activities with normal network operations. Key tools included PsExec, PowerShell, WinSCP, and LogMeIn, along with custom malware like Trojan.Rikamanu for data theft.
Galaxy 15 Satellite Interference
In 2010, the communications satellite Galaxy 15 (also known as Zombiesat) experienced a malfunction that led it to stop responding to ground commands while continuing to broadcast signals.9 The incident posed a risk of interference with other satellites’ signals, demonstrating potential vulnerabilities in satellite control systems.
Turla Group’s Espionage Campaign Targeted Satellite Internet Users
A sophisticated cyber-espionage group known as Turla, reportedly linked to Russia, targeted users of satellite-based Internet connections across the Middle East and Africa in 2015.10 By hijacking the connections of these users, Turla was able to siphon sensitive information, showcasing a unique approach to cyber espionage using satellite technology.
Can AI Securely Pilot Spaceships & Robots?
AI-driven robots are increasingly being used for tasks like satellite repair, spacecraft maintenance, and planetary-surface exploration. They are also capable of processing vast amounts of data collected during space missions, identifying patterns and insights that would be difficult for human analysts to discern — which is vital for missions that generate large volumes of scientific data. Increasingly, AI systems are being trusted with autonomous spacecraft navigation because of their ability to react faster than humans to changing conditions in space, such as avoiding space debris.
However, there is a risk of system compromise, either through cyberattacks or internal failures. Ensuring the security of AI systems that control critical aspects of spacecraft and robotic missions is paramount. The move toward AI autonomy in piloting spacecraft and robots also raises ethical questions and safety concerns. Establishing robust protocols and fail-safes to prevent unintended consequences is essential.
AI’s Role in Cislunar Exploration Missions
AI’s role in cislunar (between the Earth and the Moon) exploration missions is also increasing. AI can optimize flight paths, manage resources, and ensure mission objectives are met efficiently. On the lunar surface, AI-driven robots can conduct scientific experiments, analyze geological conditions, and even prepare for human habitation. These robots can operate autonomously, carrying out missions in harsh, unpredictable environments.
AI can also manage communications and data relay between the Earth and lunar operations, ensuring a steady flow of information even with the inherent delays in communications over such distances.
Mitigating AI Risks
Implementation of advanced encryption is essential to protecting AI-driven space systems from unauthorized access and data breaches. This includes encrypting data both at rest and in transit between space systems and ground stations.
Keeping AI systems up to date with the latest security patches is also vital. Given the remote nature of space missions, developing secure and reliable methods for updating software on spacecraft and satellites is a challenge. Anomaly detection systems can be used to monitor AI-driven space systems in real time, identifying and providing alerts of unusual patterns or behaviors that could indicate a cybersecurity threat.
It is also crucial to maintain a balance between AI autonomy and human oversight to prevent unintended consequences. Before deployment, AI systems should undergo rigorous testing and validation to ensure they perform as expected in the unique conditions of space. This includes testing for vulnerabilities that could be exploited by cyberattacks. Implementing redundancy in critical systems and ensuring that there are fail-safe modes can prevent catastrophic failures. In the event of a system compromise, these measures can maintain basic operational control and prevent total system failure.
Collaboration between agencies, governments, and industry partners is key to developing comprehensive security frameworks. Sharing knowledge and best practices can help create more secure AI systems for space applications. The use of AI in space systems also raises important ethical considerations. Ensuring transparency in how AI systems make decisions and maintaining clear lines of accountability in case of failures or unintended actions are essential.
Outlook & Recommendations
As space exploration evolves, so will the cyber threats it faces. Anticipating and strategizing against these emerging threats is crucial:
-
Future defense strategies should include advanced threat-detection systems, such as AI-driven predictive models that can anticipate and prevent cyberattacks before they occur.
-
Adaptive security architectures that can evolve with changing threat landscapes will be essential. This includes creating systems that are both reactive and proactive in their defense mechanisms.
-
Emerging technologies like quantum computing pose new threats to space cybersecurity. Developing encryption methods resistant to quantum attacks is essential.
-
Recognizing and preparing for the possibility of space-based cyberwarfare is crucial for national and global security.
-
Effective policies play a key role. Establishing standardized security protocols across the space industry can create a unified defense strategy. Implementing comprehensive regulatory frameworks can provide guidelines and best practices for securing space assets.
-
International cooperation must be part of the solution. Developing and adhering to international treaties focused on space cybersecurity can help mitigate the risks of conflicts and attacks. Harmonizing regulations across countries can facilitate a more cohesive approach to securing space assets globally.
Conclusion
Propelled by advancements in AI and robotics, space exploration presents a future brimming with possibilities. It also introduces a spectrum of cybersecurity challenges that must be meticulously addressed. Key takeaways from this article emphasize the importance of robust cybersecurity measures in safeguarding space missions:
-
Cybersecurity must be an integral part of the design and operation of space systems, not an afterthought.
-
As cyber threats evolve, so must the strategies and technologies we use to combat them. This requires ongoing R&D and adaptation.
-
The complexities of space cybersecurity necessitate a collaborative approach, involving governments, industry, academia, and international bodies.
The potential cost of cyberattacks on space missions, such as millions of dollars in lost research or catastrophic damage to critical infrastructure, further highlights the urgency of these efforts. Public awareness of these risks and the role of collaborative initiatives in mitigating them are important and should include supporting policies and organizations dedicated to advancing space cybersecurity and creating education programs for those interested in this subfield.
As we navigate the final frontier, the role of AI and robotics in space exploration will continue to grow. Ensuring a secure future in this realm requires:
-
Proactive cyber defense. Proactive and predictive cybersecurity measures should be implemented to anticipate and counteract emerging threats.
-
Ethical and responsible AI use. The deployment of AI in space must be done ethically and responsibly, with a clear understanding of potential risks and safeguards.
-
Global cybersecurity standards. Developing and adhering to global cybersecurity standards and treaties will be crucial in maintaining the security and integrity of space missions.
Specific initiatives such as the collaborative efforts between NASA and international partners for cybersecurity research and the development of global standards for space operations are indicative of the progress being made in this field.
The future of space exploration promises great discoveries and innovations, but it demands vigilance and commitment to securing this new frontier. We must embrace these challenges and work collaboratively to ensure that our journey through space is not only innovative but also secure.
The call to action is clear: support cybersecurity initiatives, advocate for stronger policies, and contribute to the safeguarding of our cosmic endeavors. As we explore the vastness of space, let us do so with the assurance that our path is secured, safeguarding the incredible potential that space exploration holds for humanity.
References
1 Manulis, M., et al. “Cyber Security in New Space.” International Journal of Information Security, Vol. 20, May 2020. (Figure 1 is being used under the Creative Commons Attribution 4.0 International License.)
2 “Large Constellations of Satellites: Mitigating Environmental and Other Effects.” US Government Accountability Office (GAO), September 2022.
3 Smith, Alexander. “Norway Calling Out Russia’s Jamming Shows European Policy Shift.” NBC News, 24 November 2018.
4 “UT Austin Researchers Successfully Spoof $80 Million Yacht at Sea.” UT News, The University of Texas at Austin, 29 July 2013.
5 Wess, Mark. “ASAT Goes Cyber.” US Naval Institute Proceedings, Vol. 147, No. 2, February 2021.
6 Greenberg, Andy. “The Untold Story of NotPetya, the Most Devastating Cyberattack in History.” Wired, 22 August 2018.
7 Foust, Jeff, and Brian Berger. “SpaceX Shifts Resources to Cybersecurity to Address Starlink Jamming.” SpaceNews, 5 March 2022.
8 Goodin, Dan. “China-Based Hackers Burrow Inside Satellite, Defense, and Telecoms Firms.” Ars Technica, 20 June 2018.
9 “Zombie Satellite Forces Evasive Maneuvers for Cable TV Spacecraft.” Space.com, 17 May 2010.
10 Lennon, Mike. “Russian-Speaking Turla Attackers Hijacking Satellite Internet Links.” SecurityWeek, 9 September 2015.



