Advisors provide a continuous flow of information on the topics covered by each practice, including consultant insights and reports from the front lines, analyses of trends, and breaking new ideas. Advisors are delivered directly to your email inbox, and are also available in the resource library.
Connecting Through the Process of Things
The Process of Things ensures value-added services such as developing smart applications around connected things and reaching out to more customers through adaptable things.
IT Governance and the Cynefin Decision-Making Framework
Through the use of the Cynefin framework, some of the challenges in IT governance become clearer.
Augmenting Human Work with AI Systems
AI systems (and robots) have the potential to make changes to our society that are as sweeping as those of the Industrial Revolution. Many jobs done today by people will become jobs that robots and AI can do better.
Achieving Information Superiority by Measuring BOM Performance
Successive or concurrent rollout of target business operating models leads to a continuously shifting baseline for some or all business design components, thus requiring careful planning and data-driven decision making. Having a framework that baselines the state of each business design component and facilitates continuous measurement assists in executive-level decision making.
The New Style of IT
Against the background of an evolving digital society, disruptive new concepts in information technology emerge. Cloud, big data, mobility, and social media are just a few of these technologies. Each is disruptive on its own, but as they converge and reinforce each other, the disruption is compounded. This is the new style of IT: the combination of these technologies, forcing organizations to rethink how IT is delivered and, more importantly, how IT is consumed to deliver business value. The new style of IT creates new paradigms and leaves behind the old premise that future IT developments are incremental.
Will Blockchain Live Up to All the Hype?
To say that blockchain (a shared, distributed, immutable ledger for recording the history of transactions) is generating a lot of attention is a huge understatement. I don't think I have seen so much excitement around a new technology since perhaps the early days of the Internet of Things (IoT) or maybe big data.
Sorry Isn’t Good Enough: Preventing Administrative Evil
This is the third Advisor in our series on combating the scourge of administrative evil. The first in this series examined three governmental IT systems — one each from the US states of Michigan, Washington, and Rhode Island — each experiencing operational failures that caused needless harm to their respective state’s citizens. In the second Advisor, we explored the idea of how poorly managed and executed government IT systems that inflict such needless harm on their citizens can rise to the level of being administratively evil. In this final installment, we discuss ways to mitigate administrative evil.
Emerging Agile Anti-Patterns
Agile methodologies, however popular they are, bring their own sets of “smells” and anti-patterns to the table, sometimes causing irreparable damage to the team. While the sources of these smells are many, one of the primary culprits is the mindset that treats Agile as “yet another methodology,” totally ignoring the cultural aspect. This article throws light on some of the prominent smells that are emerging of late in the Agile world.
Architecting in the Digital Society
Digital transformation and the new style of IT continue to evolve. How should the architecture realm then develop? More precisely, does it require us to change the way we architect solutions and interact with businesses? Are new skills required? Let’s answer these questions by considering the architecture function, discipline, and profession in that context.
Privacy and Consent in the IoT
Ubiquitous computing, ambient intelligence, and the Internet of Things (IoT): the world is quickly transforming into one in which intelligent and networked devices will be everywhere, and everything we’ve previously viewed as dumb will be infused with connectivity and awareness. The ability of objects in our environment to interact with us on this level presents a host of social challenges, some of which we are just now facing. One key challenge is how these objects will respect the privacy of the individuals they encounter. Addressing that challenge requires an understanding of privacy and, in particular, the role that notice and consent has played in mitigating privacy risks.
Technology as Innovation Driver in the Insurance Industry
The digital revolution has hit the insurance sector, with insurtech disrupting the entire value chain and customer lifecycle. New technology offers opportunities to redesign the customer experience, design new products and services, streamline processes, and increase effectiveness. The opportunities are huge; hence, they attract financial technology startups and drive investment.
Combating the Scourge of Administrative Evil, Part II
In the first Advisor in this series, we examined three governmental IT systems from the US states of Michigan, Washington, and Rhode Island. Each experienced operational failures that caused needless harm to their respective state’s citizens. In this Advisor, we argue that a strong case can be made that these failures can rise to a level of administrative evil.
Middle Management in Flux
If you start changing an organization toward an Agile mindset, there’s no real end. Agile is about creating an organization of continuous learning and the transformation is done when there is nothing new to learn, which will probably be never. This puts an enormous challenge on middle management.
What Are an Organization's Security Risks?
A corporation has various business goals, many of which involve profit expectations and ROI. Lapses in the development of a corporate architecture and security risks to data storage and processing can stifle business profit goals. Although there are a few industry and government regulations intended to strengthen a corporation’s information security posture, no regulation should be considered a one-size-fits-all solution.
Business Opportunities in the Digital Age — An Introduction
The articles in this issue present perspectives and ideas on business transformation in the digital age. We hope they will inspire and encourage you to visualize the likely future of business in your domain and to explore the opportunities it presents. Finally, we hope their insights will help you identify suitable transformation strategies and plans and, if needed, choose viable collaboration models for partnering with startups and other firms in your digital business efforts.
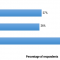
Major Threats to Sensitive Data
We are constantly reminded via media coverage of data breaches and other hacking incidents just how important it is for organizations to protect their sensitive data. Naturally, this brings up the key question: where do organizations see the biggest threats to their sensitive data emanating from? A Cutter Consortium survey that asked 50 organizations about their data-centric security and protection practices helps shed some light on this question.
Toward Collaborative Leadership
As an executive coach, I continuously hear new clients say, "All I want are results. Is it too much to expect people to deliver on their commitments?" After a few minutes of additional dialogue, we typically discover several organizational, technical, and managerial challenges that have culminated in some noticeable and negative result. In other words, I'm being asked to fix a problem that has escalated to a level that is no longer tolerable to those in leadership.
Combating the Scourge of Administrative Evil, Part I
This is the first in a series of three Advisors on poorly managed and executed government IT systems and their effects on citizens.
Agile for the Enterprise
Implementation of Agile methodologies within the enterprise can be difficult and poses significant challenges. While there is widespread agreement that the benefits are necessary, implementing Agile requires organizational change. The change is of a type that will appear risky to senior management, particularly on the apparent loss of control and by introducing a system of metrics based on satisfactory delivered code rather than on reaching established project objectives.
What Enterprises Say They Need from IT Service Providers
Business people judge services by making sense of what they experience relative to their needs. Most business decisions about IT are, and will continue to be, made in this way. This is in contrast to the current IT delivery model and the product-centric process of “define, build, and operate,” which will become less relevant as future technology and increased complexity make defining and testing product requirements difficult, if not impossible, except at runtime.
Self-Fulfilling Catastrophes
The information dysfunction endemic to politics does not stop or start with politics. It is deeply rooted in our human behavior. It is present in every aspect of our lives, starting with our own inner monologues that make up our consciousness, and extends to our families, our friends, our social networks, our organizations, our countries, and yes, to our global village.
Fulfilling the Need for Speed
The search for the ideal instantaneous speed to transmit information is well underway; it is already influencing the way we build computers and promises to revolutionize computing speed in both processing and information transmittal. This achievement has been in the making since the beginning of the 21st century: it is called quantum computing and is based on the principles of the most impacting and yet least understood branch of science, quantum mechanics, more broadly referred to as quantum physics.
Applying Lean Leadership Practices to Improve Customer Value
The guiding Lean principle is a focus on consumer value. This compels everyone to clearly understand how (or if!) their efforts contribute to consumer value. This can be a challenge, since many functions interact only with internal customers or intermediaries, having little or no line of sight to the consumer.
Security and Privacy Risks in Wearables
With today’s enormous amount of data sharing being a relatively new battleground for smart device manufacturers, the industry appears to be more about lowering costs and introducing highly marketable features. Consequently, introducing strong security is very rarely a priority — and is also a technological challenge due to relatively limited processing, energy, and network resources for wearables.
Taking a Continuous Path to an IT Portfolio Plan
IT is often highly complex and difficult for nonspecialists to understand, yet it is crucial for business executives to understand enough about IT to make far-reaching strategic decisions. IT portfolio management (ITPM) forges a critical link between the strategic planning process and the PM process, enabling management to reach consensus on the best use of resources by focusing on projects strategically aligned with the goals of the business.