Advisors provide a continuous flow of information on the topics covered by each practice, including consultant insights and reports from the front lines, analyses of trends, and breaking new ideas. Advisors are delivered directly to your email inbox, and are also available in the resource library.
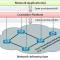
Building a Service Assurance Architecture Pattern
The IT industry struggles to deliver quality, and the majority of effort related to quality improvement is directed toward internal IT processes, rather than the results (i.e., the services) seen by customers.
Passion Poppycock
Anyone who is great, as in best in the world at what they do, is both highly passionate and disciplined about what they do. Applying your passion in business is certainly a bit more complicated than doing so for a hobby. The passion must be aligned with innate or developed skills that give you a chance to be best in the world at your work.
Architectural Integrity
Architecture representations must provide insights that take the enterprise forward, rather than seducing anxious business minds into illusory paths. While we do need to guard against the baser human emotions from hijacking the truth, it is also important to realize that integrity is threatened on a different front: a cognitive one.
The Future of Cloud Management
The overall cloud computing market is now growing rapidly. There are credible estimates that the global cloud computing market could be as much as US $84 billion by the end of 2015, and will reach $241 billion in 2020 (it was $15 billion in 2010).
The Subtle Dangers of Digital Business Transformation
The growing ability of big data to seek patterns within immense data streams; perform predictive analysis; and understand language, voice timbre, sentiment, and other attributes thought to require human intervention, raises special concerns.
A Gathering Storm
Data sovereignty poses all sorts of operational difficulties for many multinational firms.
Categorizing Neuromorphic Computing
Neuromorphic computing -- computing architectures inspired by the design of brains -- is getting serious attention from large companies. IBM is placing large bets on its Watson technology and bringing applications to several industries as well as leading the way on new types of chips that implement neural networks. Google and Facebook are both applying deep learning networks in software to tagging of images, among other uses. Neuromorphic computing is rising.
Implementing the Integrative Framework, Part II -- Scalability
In this Advisor, we focus on scalability. There are two distinct sorts of scalability: Project scalability -- addressing the ability to perform projects requiring large numbers of engineers; and Organizational scalability -- instituting common development techniques, such as Agile, consistently across an organization. While these are related, they are different. Our fundamental premise is that it is prudent to decide on a prioritization between the two.
Security in a Hyper-Connected World
Security is a major issue with the Internet of Things (IoT). The more devices you connect, the more you expose the organization to possible attack. And with all the reports of data breaches, system hackings, and cyber-espionage in the news, companies are naturally concerned about security when it comes to building IoT applications and services.
IoT in Manufacturing
The Internet of Things promises to eliminate massive information gaps about real-time conditions on the factory floor that have made it impossible to fully optimize production and eliminate waste in the past.
-- O'Reilly's David Stephenson
Insurers Embrace IoT Connected Devices
Automobile insurers have been capturing and analyzing data from sensor devices deployed in their customers' vehicles for some time. And the availability of such usage-based insurance (UBI) programs has grown considerably as insurance companies have expanded their in-vehicle offerings to various consumer groups (commuters, new drivers, etc.) and to commercial fleet operators.
From Atoms to Bits: How Physical Products and Services Are Becoming Digital
Only 100 years have passed since the Industrial Revolution and we are already in the midst of a new revolution, the latest being of a digital nature.
Learning with Lean and Agile
Both the Lean and Agile worlds encourage and value learning by doing. The Scrum framework pushes teams to engage in an ongoing PDCA (Plan-Do-Check-Act) cycle to continually inspect and adapt how they work and how they develop software.
For Scrum teams, the end-of-sprint review is where they inspect the increment of work they created during the iteration and examine what they have learned about their deliverables. Based on this knowledge, teams can review their upcoming backlog items and adjust when they feel it is necessary.
Redesigning Architecture Governance at Syngenta: A Case Study
One of my first tasks upon joining the EA team at Syngenta, a multinational agribusiness company, was to redefine the global architecture governance processes. Among my first tasks after joining the EA team at Syngenta was to redefine the architecture review board (ARB), a need that was triggered by a review of our enterprise architecture program.
Welcome to the Era of Digital Transformations
Digital technologies have become an essential part of our business environment, and of our personal lives. In 60 years or so, they have gone through an incredible journey: from simple automation of the back offices to supporting almost every aspect of the modern organization; to our homes and living rooms; to our personal use of mobile devices; to part of what we wear (clocks, glasses, bands, etc.); and, as it seems, they will become part of our bodies in the future.
The Cloud and the Diffusion of Innovation
The distinctive features of cloud computing offer many potential opportunities for business innovation, particularly given its service (and service quality) focus, coupled with the flexibility that new technology delivery mechanisms provide. However, our most recent research finds good reasons for qualifying the assumption of frictionless innovation arising from cloud adoption. The pattern, instead, may well follow past diffusions of other potentially powerful technological innovations, including the Internet itself.
Unfortunately, Following Mark Twain's Advice for Achieving Success
Back in 1887, Mark Twain noted that, "All you need in this life is ignorance and confidence, and then success is sure." We've recently had two primary examples of senior organizational management who seem to be following Twain's advice with extra zeal.
Software-Defined Networks
Traditional computer networks are complex and very hard to manage (see "Unraveling the Complexity of Network Management"). To express the desired policies, network operators need to configure each individual network device, one by one, either manually or with the use of low-level scripts. In addition to configuration complexity, network environments have to endure the dynamics of faults and adapt to load changes. Enforcing the required policies in such a dynamic environment is highly challenging.
The Service-Role Pattern as a Diagnostic Tool
There are many purposes and potential opportunities based on an architectural view of the enterprise. One that may not be readily apparent is the use of a rigorous and holistic understanding of business to detect health issues for the enterprise itself.
Practical Management: Lean and Beyond
[From the Editor: This week's Cutter IT Advisor is from authors Jim Benson's and Tonianne DeMaria Barry's introduction to the June 2015 issue of Cutter IT Journal, "Practical Management: Lean and Beyond" (Vol. 28, No. 6). Learn more about Cutter IT Journal.]
Predictive Maintenance Initiatives Are Accelerating
Predictive maintenance is becoming one of the more killer applications to arise out of the Internet of Things (IoT) and the Industrial Internet movements. We are now seeing companies ramp up their efforts to develop machine analytics with the intent of increasing equipment availability, lowering production costs, and enhancing their customer relationship and loyalty efforts.
Implementing the Integrative Framework, Part I -- Moving on from Know-How to Know-Why
In our recent workshop on the integrative framework, we emphasized that one cannot apply a single software method to all kinds of software efforts. For example, trying to develop a whole new software platform with the same process one uses to fix production bugs is a path to failure. Likewise, performance measures that are appropriate for staying on top of an input stream of production bugs differ greatly from those needed for the development of a brand new platform. Hence, to successfully manage your overall project portfolio you need to mix and match various practices and measures.
Invest Wisely in Training
I spent 20 years in the military, and one of the greatest lessons I learned was that you can't hold someone responsible for performing a task if you haven't trained them how to perform it.
AWS Steps Up Alongside FinTech Companies to Outcompete Banks
At a conference in Monaco, James Dow, VP Global Engineering at Royal Bank of Canada (RBC) stated that the banking sector now regards technology companies as serious competitors in the finance industry. Dow further pointed out that several US technology companies were each in a position to purchase the entire shareholding of multiple major banks in all-cash transactions.
Architecture's Truth in Modeling Act of 2015
What is true with financial models is even truer with enterprise models that are even more abstract and expansive in their scope. The point is that it is all too easy to create poorly thought-out models that shine radiantly as PowerPoint slides, Visio diagrams, and financial spreadsheets, but which mislead. It takes time and a labor of love to design views that are less about emotional appeal and aesthetics than they are about representing truths that are sometimes ugly, but always revealing.