Find analysis of data from Cutter's ongoing industry research efforts, brief treatments of topics that don't require the in-depth research of an Executive Report, updates on previously-covered topics, and more, in 2-4 page Executive Updates.
Flexibility vs. Control
Standards and guidelines are essential for business and allow operations to be controlled, integrated with other business processes, and performed efficiently. But process standards and frameworks also can promote rigidity and brittleness in the face of change. It is this fear of rigidity that has kept many enterprises from implementing frameworks such as ITIL, though ITIL itself actually claims to be a nonprescriptive framework.
Using DevOps Principles to Achieve Zero-Downtime Deployments
"We're going to need this deployed ASAP." I've heard this phrase hundreds of times in my career. But this time all my internal alarms sounded off.
The Architect's Mission
Organizations have missions. Specific roles have missions, too. The fact that we go to some trouble to define missions is an indication that there is some utility in doing so for entities designed to accomplish something of value. We are currently putting architects in place in our enterprises. But there are so many varied definitions of "architect" within enterprises, let alone across companies. So can defining an architect's mission help?
Promise and Growth in IaaS Amid the Darkening Clouds of Data Sovereignty
The uncertain future of cloud computing and the plethora of frowny CIO faces of a couple years ago are rapidly giving way to the acceptance -- if not embracing -- of infrastructure as a service (IaaS), at least among IT leaders. The good news is that this shift is without the typical knee-jerk and shallow skepticism or naive Panglossian enthusiasm for the next new thing. This mental shift is tempered, real, and comes with more "buy" questions than "hold" or "sell" ones.
Designing a Mobile Application: Part VI -- Designing for Mobile Security
Lately mobile security has reached a new level of public attention due to celebrity-related privacy violations, and for very good reason. Our mobile devices are becoming ever more critical to our everyday lives and hold the keys to an increasingly rich vein of all manner of sensitive data -- both personal and professional.
The Tricks and Traps of Supplier Relationship Management, Part I
The only thing you can be sure of when speaking to someone else about SRM is that he or she will think it's something different than what you mean. This leads to our first trap in Part I of this two-part Executive Update series on SRM tricks and traps at the conceptual level. What is the purpose of SRM? Is it to have good relationships? To collect data? To foster innovation?
#KeepItLegal: Laws Affecting Employer Social Media Practices
Although the growth of the Internet and e-commerce has opened a new universe of opportunities for business, this new world has its share of legal perils. Occasionally, the focus on outside perils causes companies to overlook the perils that come from a very "inside" source -- the company's own employees.
Development Intelligence: Key Dimensions
This Executive Update explores the key dimensions of development intelligence, including the types of development and organizational levels, and analytics maturity and what is measured.
Field Guide to Technology in the C-Suite
The Executive Update takes a look at the host of C-suite technology titles and discusses what they mean to enterprise's today.
Bringing Mobile Computing to Enterprise Applications
In this Executive Update we look at how to use mobile computing to broaden the impact of enterprise applications, and we discuss the complexities that such an approach entails. We examine how state-of-the-art dependency management tools can help manage this complexity and prevent systems from becoming opaque and brittle, and we see where these tools fit into end-to-end metadata architecture.
Building Privacy Controls into Software, Part II
Part I of this three-part Executive Update series provided a short overview of how information security and privacy controls are -- or more often are not -- built into software, and also reviewed the responses to the first set of questions of a Cutter survey on developing privacy-sensitive software.
Designing a Mobile Application: Part V -- Solidifying the End-to-End Mobile Application
A beautiful app with a poorly defined feature set or a terrible infrastructure ultimately doesn't stand much chance of success.
Social Media Compliance: Issues and Trends
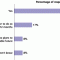
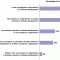
This Executive Update focuses on survey findings pertaining the extent that organizations use social media to monitor and engage customers; the areas and domains in which organizations use or plan to use social media for customer engagement; the establishment of formal policies and procedures governing enterprise social media usage; formal employee training programs for using social media; the use of social relationship management (SRM) platforms; and the key sought-after functionality of SRM platforms.
The 10 Core Principles of EA
Principles describe a stable set of guiding values. So are there any fundamental core principles that consistently guide all enterprise architecture practice? And, if so, what are they? When we know these core principles, and make them clear to all stakeholders, then the purpose and value of EA will be more visible and obvious. In this Executive Update, we explore and answer these questions, and list the 10 core principles followed by contemporary EA practice.
Tricks and Traps of the Cloud
This Executive Update is designed to help with some of the more common tricks and traps for the commercially unwary to prepare for the upcoming cloud burst. Every organization's cloud experience has been different, but there is enough collective experience out there now that we can start to learn from those who bravely went before us. These early adopters were willing to take a punt, and we are all the better for it.
The 3Ds: A Strategic Data Virtualization Methodology
Conventional data management approaches have always emphasized the physical movement of data across enterprise systems. Data virtualization (DV) introduced a paradigm shift to this approach by virtue of not physically moving data. This innovative approach has successfully addressed some of the shortcomings of the conservative approach. However, DV is not a silver bullet for all data management issues and presents its own set of challenges, as we will explore in this Executive Update.
Revisiting Service-Oriented Architecture
This Executive Updateconsiders lessons from the first 10 years of SOA and examines how advanced practitioners are putting that learning to use in next-generation service-oriented architectures.
Building Privacy Controls into Software, Part I
This Executive Update looks at the concept of privacy in software development and examines the responses of survey participants who report they actually work with "privacy-sensitive" software.
The Era of Continuous Undeclared Cyber War
Corporate leadership needs to understand that the threat is real and it is only going to get worse. Security measures need to be better observed, and GRC (governance, risk, and compliance) automation is mandatory. Importantly, risk needs to be reevaluated, particularly for those areas that are likely to be subjects of attacks.
Self-Service BI: Enabling Your Business Users to Scale the Analytics Pyramid
This Executive Update shares an approach on how you can enable self-service for a specific BI end-user community. The approach involves first assessing the analytical appetite of the user group and positioning those professionals in a three-tiered pyramid before applying the appropriate technology strategies.
Predictive Maintenance for Machine Optimization
This Executive Update examines key trends and developments around the application of predictive maintenance in industrial and enterprise operations and discusses a real-world application example intended to optimize earth-moving equipment used in mining operations.
Designing a Mobile Application: Part III -- Racing Toward the Minimum Viable Product
Change Resiliency in Organizations
Resiliency builds over time by the way an organization responds to change. Avoiding change does not build resiliency; in fact, avoiding change reduces resiliency. The most resilient organizations seek out small ways to continue to improve. In this Executive Update, Sheila Q. Cox advises you on how you can build resiliency.