Find analysis of data from Cutter's ongoing industry research efforts, brief treatments of topics that don't require the in-depth research of an Executive Report, updates on previously-covered topics, and more, in 2-4 page Executive Updates.
Software Archeology
There is a great deal of advice available on strategies for implementing new technology and for new methodologies for project management, but effective advice is relatively rare for those many sites with stranded investments in legacy IT systems and their respective support organizations.
Project Failure: Is It Real or Is It Metrics?
At a recent project management conference, one of the speakers trotted out the same old project failure statistics we've been hearing since 1995. The speaker concluded that project failure is still rampant, and if would we just try a little harder and control a little more (by installing new systems and new methods), we could finally fix the problem.
Corporate BI Tools Standardization: Vendor/Tool Selection
User Participation in Software Projects
What's Old Is New Again: A Look at Work Management Application Software
Managing work assignments is one of the top challenges in most organizations. The individuals doing the work feel scattered and overwhelmed by the volume of assignments that keep coming their way, while their managers feel caught between the proverbial rock and a hard place.
Why Large Firms Should Consider IT Outsourcing
Creating a Cooperative Vendor Relationship
Outsourcing Evolution: SWOT Assessments
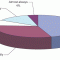
A SWOT analysis is a tool used for many purposes in business. The acronym stands for strengths, weaknesses, opportunities, and threats. As shown in Figure 1, strengths and weaknesses represent internal factors; opportunities and threats represent external factors. Strengths and opportunities are to be built or maintained; weaknesses and threats are to be eliminated or mitigated.
Integrating IT Performance Management with Business Process Management: Where Are We?
The Next Innovation in Internet Search
EVA and Technology Assessment
Why It Is Time to Break It Up
Getting Down to the Financial Basics of Business Technology
The Myth of Guaranteed Delivery
Several recent architecture assignments have brought up what I am starting to think of as a new urban myth: guaranteed delivery of products unequivocally guarantees delivery of messages. This is my chance to rant out this annoyance.
Software Practices and Project Success
What Does It Take to Assemble a Successful Software Project Team? Part II: Agile Adventurers
Thinking the Unthinkable
Defining and Determining Adequate Security
Editor's note: This Executive Update is excerpted from the Software Engineering Institute's Governing for Enterprise Security (©2005 Carnegie Mellon University). Permission has been granted to Cutter Consortium to reproduce.
Measurement: The Key to Successful Governance
The Time Has Come for a Chief Offshoring Officer
The quip to emerge from business process offshoring's growing prominence is this: if you want to avoid being laid off from offshoring, then become the person who manages all the offshoring initiatives in your organization. Surely someone has to hang around to turn off the lights at the end of the day.
Business Technology Trends to Consider
So what the hell is going on in our industry anyway? Should we be happy, or should we be worried? Here are five things to think about.