Find analysis of data from Cutter's ongoing industry research efforts, brief treatments of topics that don't require the in-depth research of an Executive Report, updates on previously-covered topics, and more, in 2-4 page Executive Updates.
Performance Metrics: The Seven Deadly Sins -- Part II
Software Project Failures: Part III -- The Software Samurai
Building Security into Software Development Lifecycle Processes
In recent years, a number of seminal books have helped to define the software security field [1, 2, 8]. The approach to "building security in" introduced in these books has been enhanced and expanded by practitioners and published in various technical articles, including the "Building Security In" series in IEEE Security & Privacy.
Architecture for the Hard to Please
Enterprise architecture, business architecture, technology architecture, information architecture, federated architecture, domain architecture, product family architecture, platform architecture, solution architecture, system architecture, software architecture ...
Performance Metrics: The Seven Deadly Sins -- Part I
Of PMOs, VMOs, and XMOs: Why So Many Management Offices?
Everyone wants new management offices. It seems that a preferred response to management problems of many kinds is to create a new office responsible for something fairly specific. The ones that come immediately to mind are project management offices (PMOs), process management offices (PMOs again -- causing, of course, some confusion among the acronym crowd), and vendor management offices (VMOs). What are these offices, and who are these people? And why are there so many of them?
Avoiding the Risks of Outsourcing: Six Legal Points to Ponder
One of the seemingly eternal debates in information technology is whether to handle development and other IT tasks internally or to outsource them to a domestic or foreign vendor. Outsourcing offers a number of obvious benefits, such as saving money, reducing the cost of overnight processing by shifting work to an overseas vendor, or simply fulfilling a short-term need for additional skilled technical talent without having to hire new employees.
Vision-Centered Change: Fitting Process Improvement with the Culture
There's an old saying: "If you don't know where you are going, any road will get you there." This is especially true of process-improvement initiatives. Most change initiatives start out with a clear sense of goal (better, faster cheaper) yet stumble when all the energy and effort seem to fail to produce lasting change. How does the implementation fail if the vision seems clear?
The Eastern European Outsourcing Market: Focus on the Czech Republic
Central and Eastern Europe (CEE), 1 including the Czech Republic, Poland, Hungary, Romania, and Latvia, has been ranked among the top locations for outsourcing IT work. 2 Yet knowledge of sourcing to this region, with its advantages and disadvantages, is limited and rather vague. In most books on IT sourcing, these countries appear under the heading of "other," following India, China, and Russia, and little information is provided about sourcing to these locations [7].
Lessons Learned (And Not)
Early last year, the FBI finally cancelled its Virtual Case File (VCF) system project after spending more than US $100 million on it.
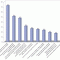
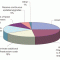
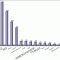
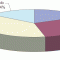
Corporate BI Tools Standardization: Spending Trends
Software Project Failures: Part II -- Ignoring the Warning Signs
Critical Path: Assessing the Effectiveness of Change Management Processes
All change must be auditable, and all unauthorized change must be investigated.